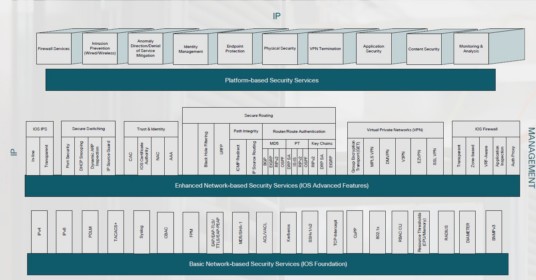
Before examining which devices to deploy in secure network architecture, it would be useful to determine where the trusted network boundaries or perimeters are. Here is a simple definition of a network perimeter:
Network perimeters are established by Routers. A network perimeter is a logical boundary between parts of the network with differing levels of trust.
The Cisco Self-Defending Network encompasses:
Network and endpoint security – The Cisco Self-Defending Network integrates Router, VPN, IPS, and other security services into network devices and endpoints to create an integrated, adaptive, and collaborative defence system.
Content security – Cisco product and security innovations extend network defenses beyond the traditional network perimeter to protect data in motion, incorporating e-mail, Web interactions, instant messaging systems, and other applications that require content inspection and control.
Application security – A Cisco Self-Defending Network extends protection to applications and data, providing XML and HTML inspection capabilities and fine-grained application control.
System management and control – Today’s Cisco Self-Defending Network integrates sophisticated policy, identity, and reputation services with powerful enforcement capabilities. These technologies unify disparate network, endpoint, content, and application security services, and provide businesses with unprecedented visibility and control.
Constructing a Cisco Self-Defending Network
Policy Management – Cisco Security Management.
Threat Management – Cisco Security MARS.
Endpoint Security – Cisco NAC Appliance and Cisco Security Agent.
Network Infrastructure – Cisco IPS Sensor Software, Cisco IOS Software, and Cisco ASA Adaptive Security Appliances.
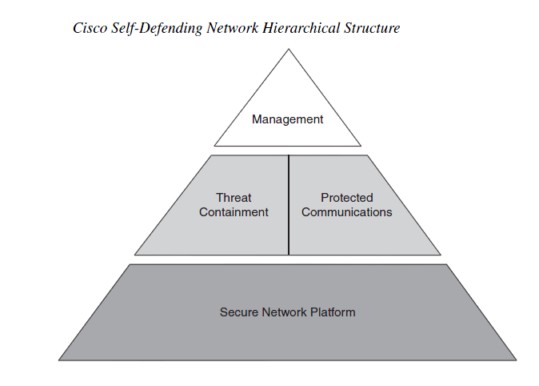
The components of a Cisco Self-Defending Network are three technical controls and one administrative control.
Secure Network Platform – Use devices where security is an integral, fundamental network feature. This is a technical control. Secure communications leverages on advanced technologies such as VPN services (both IPsec and SSL), as well as secure voice and wireless, to maintain confidentiality while increasing flexibility and in a cost-effective manner.
Threat Control and Containment – Employ advanced technologies that mitigate the effects of outbreaks and ensure employee productivity in a constantly-evolving threat environment. This is a technical control.
Secure Communications – Configure devices to ensure the confidentiality and integrity of data, voice, and wireless communication. This is a technical control.
Operational Control and Policy Management – Deploy a suite of controls that creates a framework for operational control and policy manage. Employs network management solutions that aid in the speed and accuracy of policy deployment and provides visibility throughout the network to monitor end-to-end. The controls also help in enforcement of the security policy and manage workflows.
Security Challenges in Modern Networks
In today’s world, the enterprise and organizational networks are complex, distributed environments meant to server various purposes. There are lots of security related challenges in dealing with such networks which have been discussed below, before we proceed to learn about the Cisco self defending network architecture.
Some of the most important and intriguing challenges faced by modern networks are as follows:
- Sophisticated attacks – gone are the days when attackers were novices or hardly had any tools at their disposal. Nowadays attackers use increasingly malicious and deadly tools to carry out attacks and the propagation times are on the decline.
- Time available for defending against new attacks is increasing becoming shorter and shorter. In fact, the window for the security personnel to deal with new types of threats has been reducing drastically, having shrunk literally to seconds and/or minutes instead of the earlier time frame of days or perhaps weeks
- The chain is only as strong as its weakest link and this is certainly a harsh reality in terms of network attacks. Even though the use of most sophisticated tools for security is on the rise, a slight loophole here or there would do away with all the arrangements.
- It is becoming increasingly difficult to identify threats and attacks amongst complicated networks which possibly contain multiple devices from various vendors, using various platforms and so forth.
SDNA Model
In lieu of the above challenges, which only represent a partial picture of the vast problems of network security, companies such as Cisco have come to realize that each and every device pertaining to a network should have its part to play in the security of the network. The devices should interact in a cooperative manner in order to mitigate the attacks. This is the core idea behind the Cisco self defending network architecture.
The self defending network strategy is based upon three main principles which are discussed as follows.
- Integration – this principle ensures that all network devices have their share in policy enforcement as well as implementing the defense strategy.
- Collaboration – this principle ensures that all the devices and services work in collaboration and harmony to achieve the final goal which is the prevention of attacks
- Adaptation – this refers to the proactive security approach adopted for automatic prevention of threats
Systems in SDNA
In total there are four systems which can be said to be a part of this architecture. The term system refers to the combination of hardware and software required to implement the previously mentioned principles of self defending architecture.
- Cisco security management includes the policy management features of SDNA
- Cisco security MARS includes provision for threat management
- NACA and Security Agent for Endpoint security
- IPS, IOS software and ASA Adaptive security appliances for Network Infrastructure
Control Components of SDNA
- Secure network platform is a technical control and it uses devices for implement security as the main feature of the network
- TCC or threat control and containment refers to another technical control which aims at improvising upon productivity of employees despite the rising level of threats in a flux of threat environment.
- A technical control is deployed to ensure that all the communications of data and voice are confidential and this is referred to as secure communications component.
- OCPM refers to operations control and policy management which is an administrative control aimed to ensure end to end security.
Layers of Security
The self defending network architecture can be better understood by considering the diagram below which shows the basic manner in which security levels are deployed to the core IP network of an organization.
- The star in the image below represents the core IP network of the organization.
- The circle surrounding this star denotes the Security Point Services such as firewalls, IPS, access control, antivirus etc.
- The next module to be incorporated would be the advanced technologies and services including automated threat response, dynamic DDoS Mitigation and so on
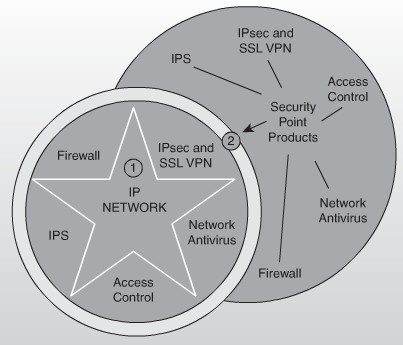
Figure : Secure Network Services
In actual practice it is not possible to deploy these services using any particular hardware product or software application; hence Cisco uses a wide variety of products which can be used in a judicious manner to implement the same. Some of these devices are as follows
- Cisco PIX 500 Series Security Appliances
- Cisco ASA 5500 Series Adaptive Security Appliances
- Cisco Security Manager
- Cisco Security MARS
- . IDS and IPS appliances
This is just a small list of devices used for SDNA. In the subsequent sections we will discuss a few of the above mentioned components.
Intrusion Detection System
Intrusion detection system refers to the hardware and/or software whose purpose is to listen to network traffic in a passive mode in order to find out any possible malicious traffic. The IDS does not fall directly within the traffic flow hence it offers no resistance to the flow of normal traffic.
The IDS may not take direct action, but informs the other devices of possible malicious activity by sending an alert to the management station, based on which those devices can stop traffic flow. It also means that only further traffic will be stopped while the initial malicious packets could flow in causing damage.
Intrusion Protection System
In contrast to IDS, the IPS or intrusion prevention systems are active devices which are directly in the path of traffic flow. They listen to network traffic and decide whether to allow or permit that traffic. It offers much better protection since even the original malicious traffic is stopped as compared to the IDS where only subsequent packets are dropped.
Approaches to Intrusion Detection and Prevention
- Signature based approach to intrusion detection is based on identifying known signature patterns of malicious code against the contents of the packet. Normally this is done if that pattern also correlates to a specific service or port thus reducing the number of packets to be examined.
- As the name itself suggests, policy based approach uses certain types of algorithms to ensure that any malicious activity such as say port scanning is detected. It defines the various factors which must be fulfilled for the trigger to trip. This type of approach can be used for both simple statistical events as well as complex relationships.
- Anomaly detection is based on finding out deviations from pre-defined patterns of traffic. This type of approach is more suitable for relatively smaller networks and could be difficult to implement of large networks. The normal behavior pattern could either be pre-fed into the system or based on normal learning method.
- Honeypot approach uses a dummy server which is deliberately kept to attract hackers and attackers. Hence it acts like a trap where the attackers get trapped while the real network is safe.
Host-Based IPS
Host based IPS or HIPS refers to a type of intrusion prevention system where each individual host on a network is examined for protection purposes. It is mainly used to thwart higher level attacks as it is not much useful in thwarting lower level attacks, for example attacks targeting layers 1 through 3 of the OSI model.
Network-Based IPS
The network based IPS or NIPS is in contrast to HIPS and protects the entire network or critical parts of the same. It is very useful for protection against lower level attacks and also can detect packets having malicious content which would otherwise be overlooked by the simple filtration process of a normal firewall.
