AAA provides security with a scalability degree which is higher than line-level and privileged-EXEC authentication. Unauthorized access, dialups and internet environments are potential set ups for network trespassers to gain access to sensitive network, services and equipments. AAA ensures a security system which is systematic and scalable. The entire concept is based on modular architecture, that is, Authentication, Authorization and Accounting. The functional components that AAA intends to provide:
- Authentication: This is used to identify users by login identification and a password. This component answers the question ‘who you are?’ It also does the purpose of determining whether the user is the person he claims to be. The entity which is seeking access is the client and the one verifying the credentials is the server. This challenges the user for a response before allowing the user access to the network. It can also be configured to support encryption depending on the security options that are selected. The credentials are verified using passwords and digital certificates.
- Authorization: After authentication is done it is time for authorization. What all a user is determined to access on the network is determined by authorization. It is the process of granting or refusing access to services provided on the network. The criterion of determining is the access policy that is specified for specific entities. At this stage IP addresses may also be issued as in the case of using VPN. In the Cisco IOS, AAA authorization can be done with a name list authorization method. Access privileges generally pertain to usage of services like IP address filtering, address assignment, quality of service, compulsory tunneling etc.
- Accounting: This is the last ‘A’ and it stands for accounting. Security information is collected under this and can in turn be used for billing, reporting and even auditing. It is a means to check what the user does once he is authorized to have access to the network. It maintains a complete record of what the user did while he was logged on the system. It maintains a track of the resources consumed by various users. Generally accounting pertains to information about the user, the nature of service used, the beginning of the service and the end of it.
The processes authorization and accounting are made to work only after the first stage of authentication has been cleared. It is possible that either authorization or accounting or both be used. This facility provides a great amount of flexibility. It is up to the systems administrator to decide on these facilities.
AAA Access Modes
There are two modes that are available for access. These modes are:
- Character Mode: This mode is used on the vty, TTY, AUX, and CON ports. These ports are most commonly used while configuring devices.
- Packet Mode: This mode is used on the ASYNC, BRI, PRI, and serial ports. It is also used on dialer profiles and dialer rotaries. This mode is used when the user is trying to communicate with a different device.
The table given below illustrates the various port sand their associated modes.
|
Interface |
Mode
|
Description |
|
AUX |
Character
|
Auxiliary DTE Ports |
|
Console |
Character
|
Console Port |
|
TTY |
Character
|
Async Port |
|
Vty |
Character
|
Virtual Terminal Line |
|
PPP |
Packet |
PPP on serial or ISDN interface
|
|
Arap |
Packet |
AppleTalk Remote Access (ARA) protocol on serial interfaces |
|
NASI |
Packet |
NASI Packet NetWare Access Server Interface on serial interfaces |
Implementing AAA
The AAA access control is supported by Cisco networking products by using line passwords, a local username/password database, or remote security server databases. For a small group of network users a local security database is configured in the router by using the username xyz password ( or secret) strongpassword command. For multiple network devices and users a remote security database is set as a separate server to run AAA security protocol. The figure given below illustrates the cases well.
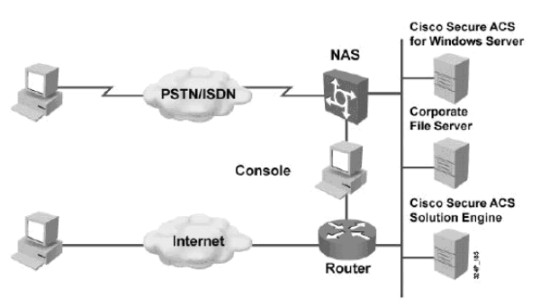
Figure 1: Implementing AAA
An example of AAA implementation is authenticating access of corporate LAN through dialup or Internet by remote users. Another example is authenticating administrators accessing the router console port, aux port and vty ports.
There are three ways that have been provided by Cisco for implementing AAA services. These methods can be used for implementing AAA on routers, network access servers (NASs), and switch equipment, as shown in the above figure. These methods are:
- Self Contained AAA: As the name suggests AAA services in this method are self-contained in the router or NAS itself. It is also known as local authentication.
- Cisco Secure ACS for Windows Server: In the second method, AAA services on the router or NAS work by contacting an external Cisco Secure Access Control Server (ACS) for Windows System.
- Cisco Secure ACS Solution Engine: In the third method, AAA services on the router or NAS contact an external Cisco Secure ACS Solution Engine for user and administrator authentication.
Configuring AAA
AAA can be configured on a system using both CLI as well as SDM.
Using the CLI
Configuring AAA using CLI is not a complex job. It can be configured by using both RADIUS as well as TACAS+.
Configuring using RADIUS: The example given below describes how AAA can be configured using RADIUS.
aaa new- model
radius-server host 1 0. 1 0. 1 . 5
radius-server key TheRADIUSServerKey
username root password MySecretPassword
aaa authentication ppp mydiallist radius local
aaa authorization network radius local
aaa accounting network mynetwork start- stop group radius
Configuring using TACACS+
aaa new- model
tacacs-server host 1 0. 1 0. 1 . 5
tacacs-server key TheTacacsServerKey
username root password MySecretPassword
aaa authentication ppp mydiallist tacacs+ local
aaa authorization commands 15 tacacs+ if-authenticated none
aaa accounting network start- stop tacacs+
AAA-Related Commands
- Command aaa new-model: This command is used to enable AAA on the router.
- Command no aaa new-model: This command is used to disable AAA on the router.
- Command username root password : This is not a AAA specific command. It is used to specify a username and a password.
- Command aaa authentication ppp : This command is used for specifiying the AAA authentication methods which are used on serial interfaces.
- Command aaa authorization: This command sets the parameters that restrict network access for a user.
- Command aaa accounting: This command enables accounting for services that have been requested.
Using SDM
Security Device Manager (SDM) is the alternative method of configuring AAA. SDM uses a graphical interface for configuring. It also makes the process easier and quicker. The steps are as follows:
- Start SDM and connect to the router
- Click on the configure button on the top of the screen
- The screen will show the Additional Tasks list
- Choose AAA to start the configuration process
- A pop up will appear in which click on yes
The five steps mentioned above equal the AAA new-model CLI command. Using the local database, the vty and the console ports automatically configure. Click on yes to continue.
Adding AAA Servers
To add the servers, in the Additional Tasks choose AAA servers. Then click on Add. This will open the server dialog box. The RADIUS server is the default server. While choosing RADIUS, there is an option to specify the UDP timeout, authorization and accounting ports, configuration and changing of encryption key.
The TACAS+ uses TCP and not UDP. Ports for authorization and accounting cannot be selected. When the TACAS_ server is being used the option of a single server is made available. While using this option a single connection is opened for all three purposes rather than having three individual connections for authentication, authorization and accounting. Even with TACAS+ configuring timeout and keys is possible just as in RADIUS.
