Cisco CCENT Security Part II – Collision and Broadcast Domains
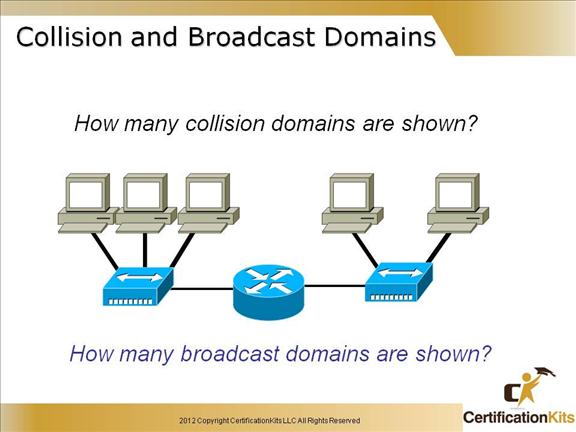
Two collision domains, two broadcast domains.
A router breaks up both collision domains and broadcast domains and a hub breaks up no collision domains.
Cisco CCENT Collision and Broadcast Domains
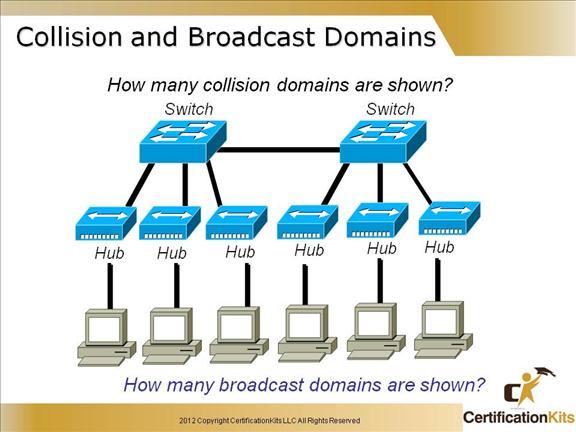
One broadcast domain, six collision domains are shown. The Switch to Switch link is not considered a collision domain as it is a full duplex link in which collisions are not applicable.
By default, switches break up collision domains with each port, but are one broadcast domain by default.
Cisco CCENT Collision and Broadcast Domains
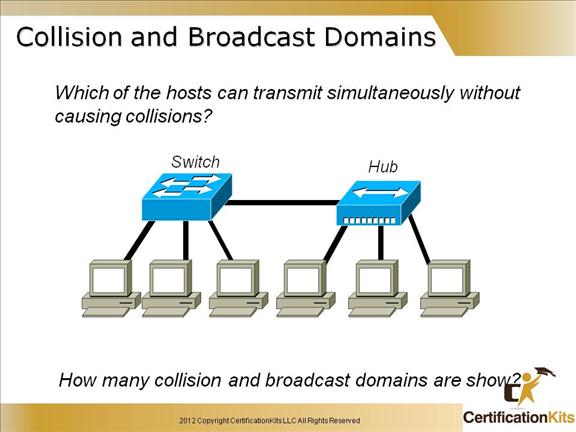
Only the hosts connected to the switch can transmit simultaneously without causing collisions.
Four collision domains are shown, one broadcast domain.
By default, switches break up collision domains with each port, but they are only one broadcast domain by default.
Cisco CCENT Hardware and Logical Addressing
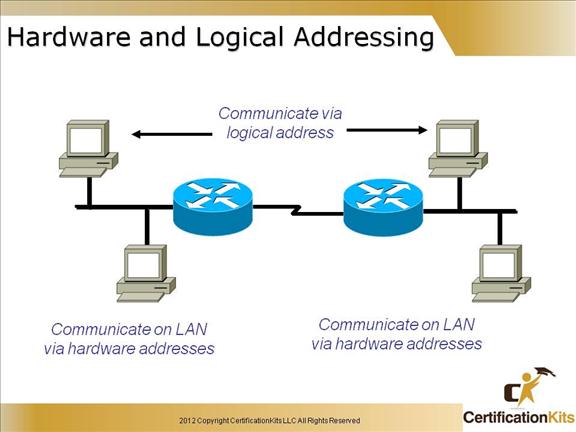
Hardware Address
Uniquely identifies a host on a LAN
Logical Address
Uniquely identifies a host on an internetwork
Cisco CCENT Physical Typologies
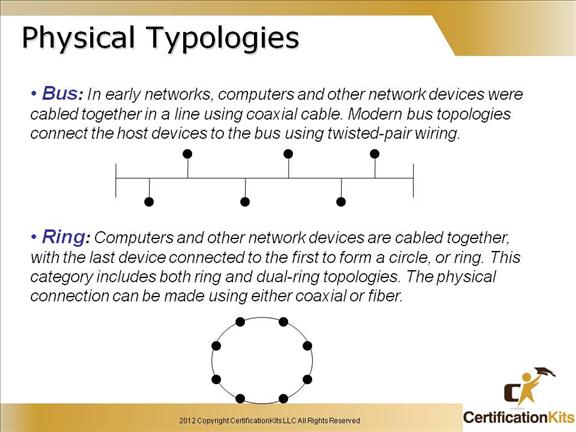
The Physical Topology refers to the cabling and layout of the physical network devices. There are different types of cabling (i.e. twisted pair, fiber, and in the shared ethernet days coaxial – used in bus topologies).
Examples of different types of physical topologies include Bus, Ring, Star and Mesh. Star and Mesh are covered on the following slide.
Cisco CCENT Physical Typologies
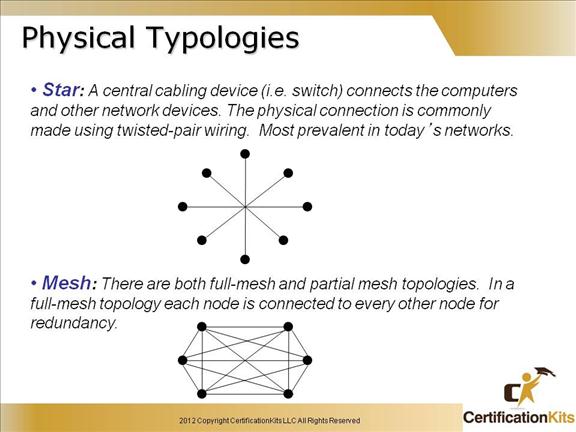
The number on connections required for a full mesh is calculated utilizing the following formula where n is the number of nodes:
(n * (n – 1)) / 2
For example is a 6 node network like what is in the slide, the calculation would be:
(6 * (6 – 1) / 2 = (6 * 5) / 2 = 30 / 2 = 15
Cisco CCENT Connecting to the Internet
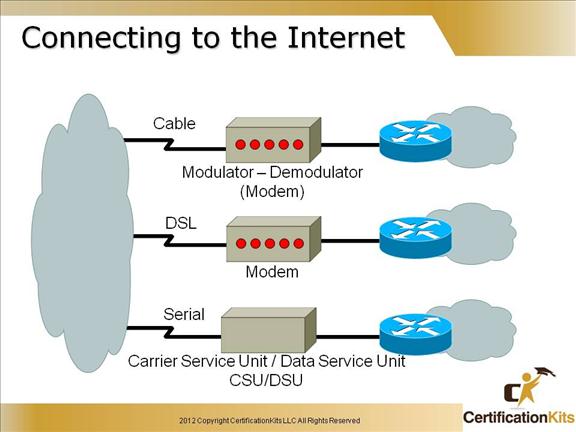
There are multiple ways of connecting to the Internet. Some of the common ways are via Cable, DSL and Serial lines.
Cable uses the cable television (CATV) infrastructure. Serial links uses the classic digital local loops. DSL uses the existing telephone lines. In the case of DSL and cable, the incoming lines are terminated into a modem that converts the incoming digital encoding into Ethernet format. In the case of serial, this is done by CSU/DSU. In all three cases (DSL, cable, and serial) the Ethernet output is sent to a router that is part of the customer premises equipment (CPE).
Cable and DSL connections utilize a modularor-demodulator (modem) to interface with the WAN while serial lines interface with a Carrier Service Unit (CSU) / Data Service Unit (DSU).
Cisco CCENT Common Threats to Physical Installations

Hardware threats: The threat of physical damage to the router or switch hardware. Mission-critical network equipment should be located in locked room with restricted access to only authorized personnel.
Environmental threats: Threats such as temperature extremes (too hot or too cold) or humidity extremes (too wet or too dry). The room should have dependable temperature and humidity control systems. If possible, remotely monitor and alarm the environmental parameters of the room.
Electrical threats – Threats such as voltage spikes, unconditioned power (noise), insufficient voltage (brownouts) and total power loss. Network equipment should be utilize redundant power supplies, be placed on uninterruptible power supply (UPS) for mission critical systems and monitored.
Maintenance threats: Maintenance threats include poor handling of equipment (ESD), lack of spares, poor cabling. Clearly label all equipment cabling and secure the cabling to equipment racks to prevent accidental damage, disconnection, or incorrect termination. Do not leave a console connected to and logged into any console port. Always log off administrative interfaces when leaving a station.
Cisco CCENT Network Security – Closed Networks
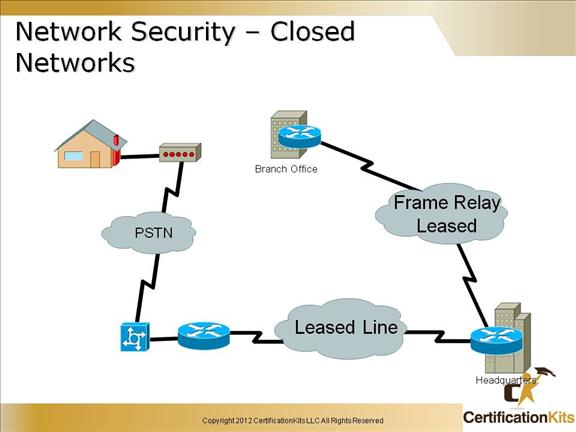
Closed Network – No outside connectivity (leased lines / dedicated circuits), networks designed in this way can be considered safe from outside attacks. It provides connectivity to only known trusted parties and sites. While it is considered safe from outside attacks, internal threats still exist.
Cisco CCENT Network Security – Open Networks
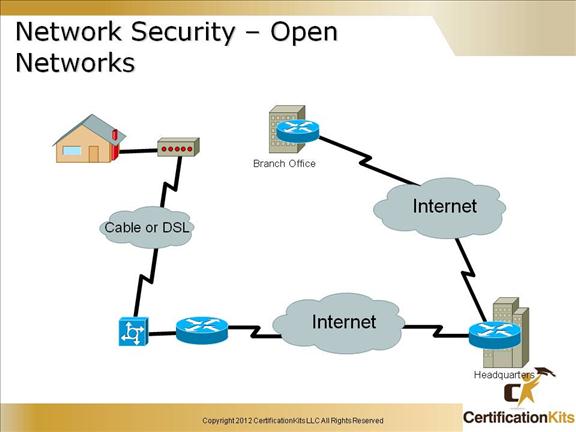
Open Network – Corporate networks require access to the Internet and other public networks. It is not uncommon for corporate networks have several access points to public and other private networks. Securing open networks is extremely important. Open networks have not only internal threats but external threats as well.
Cisco CCENT Balancing Network Security

It is difficult to find a balance between securing the network while still allowing valid traffic required to support business.
Security has moved to the forefront of network management and implementation. Most businesses survival depends on allowing open access to network resources and to ensure data and resources are as secure as possible. This is a very daunting task.
Cisco CCENT Common Attack
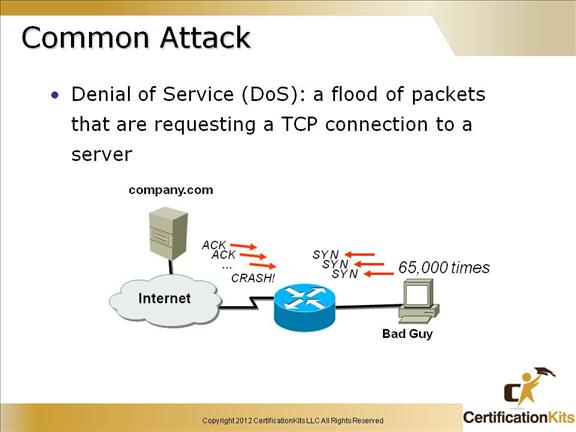
There are numerous different classes of attacks. Some of which may include passive monitoring of communications, exploits by insiders with access to the system, distributed attacks from remote sites, close-in attacks and active network attacks.
One common attack is a Denial of Service (DoS) attack. This is an attempt to make a computer resource unavailable to its intended users.
One common method of this attack involves saturating the target (victim) machine with external communications requests. In doing so, it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. Generally speaking, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
Cisco CCENT Security Appliances
Above are definitions of Intrusion Detection System (IDS) and Intrusion Prevention System (IPS).
