Cisco CCENT Introduction to TCP/IP Part I
This chapter will cover the basics of the TCP/IP model and an introduction to IP addressing and subnetting.
Cisco CCENT Introduction to TCP/IP
The Transmission Control Protocol/Internet Protocol (TCP/IP) suite was created by the Department of Defense (DoD) to ensure and preserve data integrity, as well as maintain communications in the event of catastrophic war.
So it follows that if designed and implemented correctly, a TCP/IP network can be a truly dependable and resilient one.
The Internet is built on a TCP/IP network.
Cisco CCENT User Datagram Protocol vs. Transmission Control Protocol
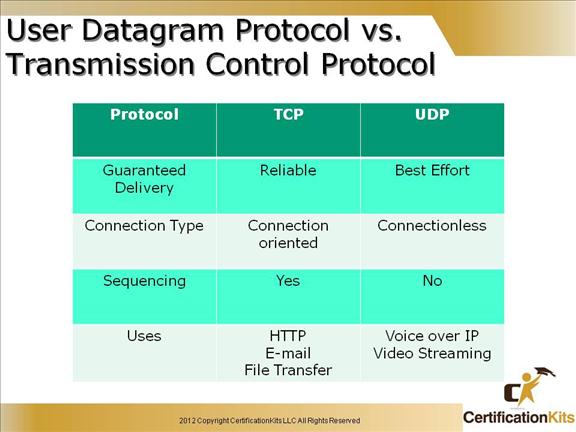
Reliable (Connection Oriented) – TCP is a reliable protocol that resides at the transport layer of the OSI reference model. It accounts for retransmission of lost data guaranteeing reliable delivery while also providing sequencing of packets so they can be re-ordered accounting for packet received out of order. Examples of applications that utilize TCP as a transport are HTTP, E-mail and FTP just to name a few.
Best Effort (Connectionless) – UDP is a best effort protocol that resides at the transport layer of the OSI reference model. It has much less overhead than TCP. It does not retransmit packets lost in transit nor does it provide sequencing to account for packets received out of order. A couple of examples of applications that utilize UDP are Voice over IP an Video Streaming.
Cisco CCENT Transmission Control Protocol (TCP)
Since the upper layers just send a data stream to the protocols in the Transport layers, the Internet layer then routes the segments as packets through an internetwork.
The packets are handed to the receiving host’s Host-to-Host layer protocol, which rebuilds the data stream to hand to the upper-layer applications or protocols.
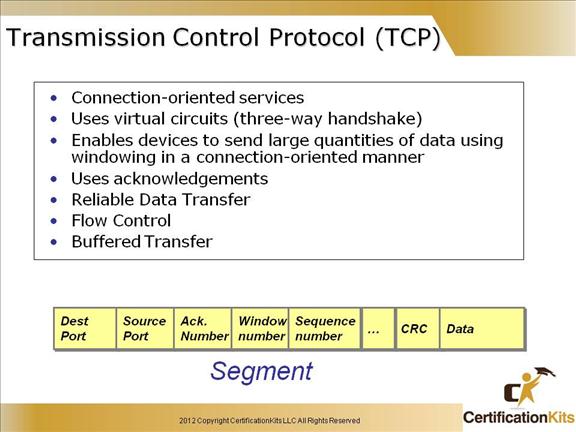
TCP creates a reliable sessions by setting up a virtual circuit (TCP connection), which includes acknowledgements, sequence numbers and windowing (flow control). TCP utilizes a three-way handshake to establish the TCP connection. The connection is uniquely identified by a combination of source ip address/port number and destination ip address/port number.
Cisco CCENT TCP Header
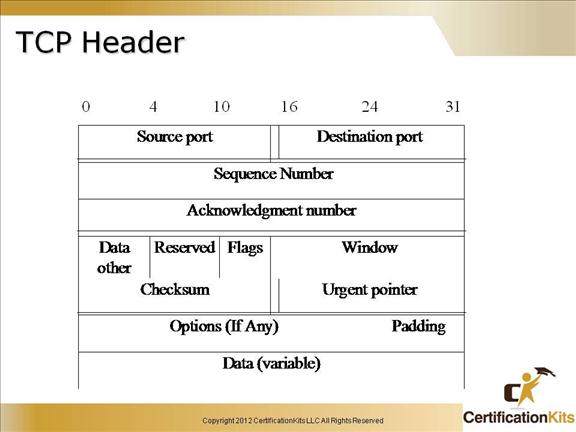
Source port – Identifies the TCP source port.
Destination port – Identifies the TCP destination port.
Sequence number – Usually specifies the number assigned to the first byte of data in the current message. On connection establishment, identifies the initial sequence number to be used in the connection.
Acknowledgement number – Contains sequence number of the next byte of data the sender of the packet expects to receive.
Data offset – Indicates the number of 32 bit words in the TCP header.
Reserved – For future use.
Flags – Control information.
Window – Specifies the size of the sender’s receive window or in other words buffer space.
Checksum – Indicates whether the header was damaged in transit.
Urgent pointer – Points to the first urgent data byte in the packet.
Options – Specifies various TCP options.
Data – Contains upper layer information.
Cisco CCENT TCP Port Numbers
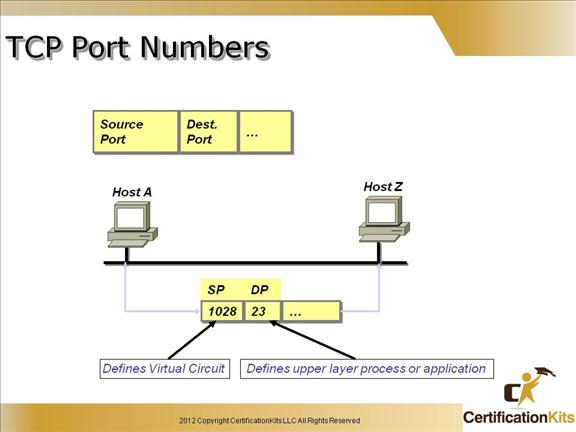
Example port numbers:
HTTP (80), HTTPS (443) Telnet (23), FTP (21), SMTP (25): TCP
TFTP (69), SNMP(161): UDP
Originating-source port numbers are dynamically assigned by the source host and will equal some number starting at 1024. 1023 and below are defined in RFC 1700, which discusses what are called well-known port numbers.
Virtual circuits that don’t use an application with a well-known port number are assigned port numbers randomly from a specific range instead. These port numbers identify the source and destination host in the TCP segment.
The different port numbers that can be used are:
Numbers below 1024 are considered well-known port numbers and are defined in RFC 1700.
Numbers 1024 and above are used by the upper layers to set up sessions with other hosts, and by TCP to use as source and destination addresses in the TCP segment.
Cisco CCENT Setting Up A Reliable Session (Virtual Circuit)
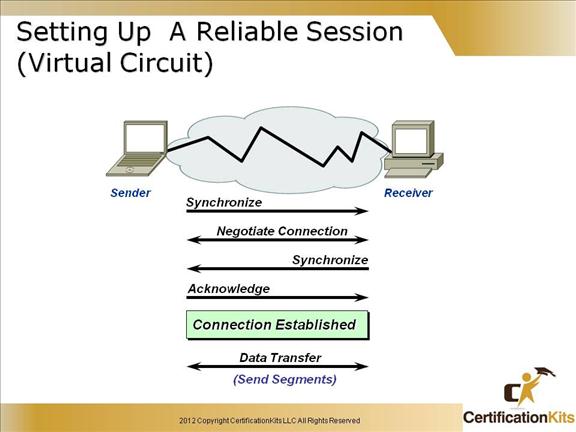
In reliable transport operation, one device first establishes a connection-oriented session with its peer system. This is called a call setup, or a three-way handshake.
Data is then transferred, and when finished, a call termination takes place to tear down the virtual circuit.
TCP uses a three-way handshake to establish a connection. The TCP three-way handshake is described in detail on the following slide.
Cisco CCENT TCP Connection Establishment
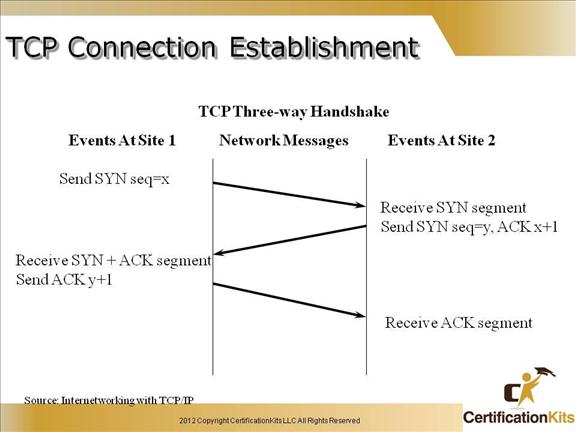
Shown in the slide is the TCP three way handshake used in establishing all TCP connections. The important thing here is the bits that are set with each packet (i.e. SYN, SYN+ACK, ACK).
As depicted, to establish a connection, TCP uses a three-way handshake. Before a client attempts to connect with a server, the server must first bind to a port to open it up for connections: this is called a passive open. Once the passive open is established, a client may initiate an active open. To establish a connection, the three-way (or 3-step) handshake occurs:
1. The active open is performed by the client sending a SYN to the server. It sets the segment’s sequence number to a random value A.
2. In response, the server replies with a SYN-ACK. The acknowledgment number is set to one more than the received sequence number (A + 1), and the sequence number that the server chooses for the packet is another random number, B.
3. Finally, the client sends an ACK back to the server. The sequence number is set to the received acknowledgement value i.e. A + 1, and the acknowledgement number is set to one more than the received sequence number i.e. B + 1.
At this point, both the client and server have received an acknowledgment of the connection.
Cisco CCENT TCP Connection Termination
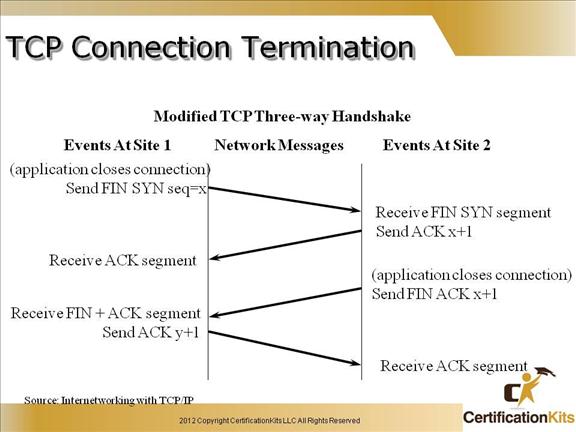
Shown in the slide is the modified TCP three way handshake used in gracrfully terminating all TCP connections. The important thing here is the bits that are set with each packet (i.e. FIN+SYN, ACK, FIN+ACK).
Cisco CCENT TCP Flow Control
Data integrity is ensured at the Transport layer by maintaining flow control and by allowing users to request reliable data transport between systems.
Flow control prevents a sending host on one side of the connection from overflowing the buffers in the receiving host—an event that can result in lost data.
Random Early Detection (RED) is a congestion avoidance mechanism that takes advantage of TCP’s congestion control mechanism.
Positive Acknowledgment and Retransmission (PAR) protocol consists of a sender, a receiver, and two unreliable communication channels for messages and acknowledgements.
A new message is sent only when the preceding one has been acknowledged. The sender detects the loss of a message (or acknowledgement) by using a timeout.
Cisco CCENT Positive ACK with Retransmission
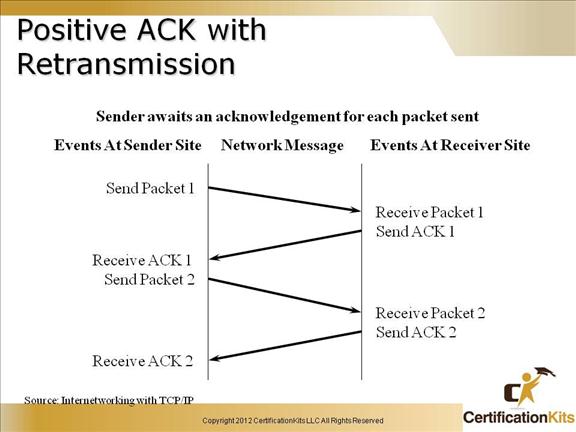
Each TCP packet send is ultimately acknowledged. If it is not acknowledged, it is retransmitted after a specified period of time.
Cisco CCENT Positive ACK with Retransmission
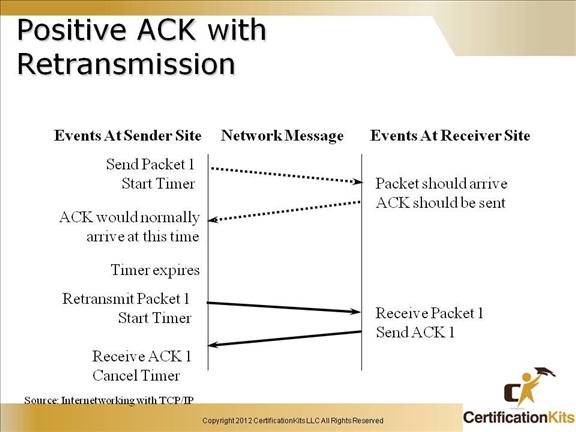
The slide above shows a packet that is sent that sender does not receive an acknowledgement prior to the timer expiring so the packet is retransmitted.
Cisco CCENT TCP Sliding Window

Buffers are used at each end of the TCP connection to speed up data flow when the network is busy. Flow Control is managed using the concept of a Sliding Window. A Window is the maximum number of unacknowledged bytes that are allowed in any one transmission sequence, or to put it another way, it is the range of sequence numbers across the whole chunk of data that the receiver (the sender of the window size) is prepared to accept in its buffer. The receiver specifies the current Receive Window size in every packet sent to the sender. The sender can send up to this amount of data before it has to wait for an update on the Receive Window size from the receiver. The sender has to buffer all its own sent data until it receives ACKs for that data. The Send Window size is determined by whatever is the smallest between the Receive Window and the sender’s buffer. When TCP transmits a segment, it places a copy of the data in a retransmission queue and starts a timer. If an acknowledgment is not received for that segment (or a part of that segment) before the timer runs out, then the segment (or the part of the segment that was not acknowledged) is retransmitted.
Cisco CCENT TCP Sliding Window
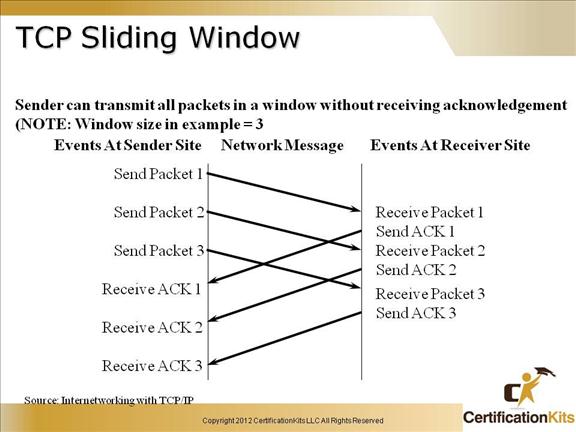
TCP Sliding Window Operation:
1. The current sequence number of the TCP sender is y.
2. The TCP receiver specifies the current negotiated window size x in every packet. This often specified by the operating system or the application, otherwise it starts at 536 bytes.
3. The TCP sender sends a datagram with the number of data bytes equal to the receiver’s window size x and waits for an ACK from the receiver. The window size can be many thousands of bytes!
4. The receiver sends an ACK with the value y + x i.e. acknowledging that the last x bytes have been received OK and the receiver is expecting another transmission of bytes starting at byte y + x.
5. After a successful receipt, the window size increases by an additional x, this is called the Slow Start for new connections.
6. The sender sends another datagram with 2x bytes, then 3x bytes and so on up to the MSS as indicated in the TCP Options.
7. If the receiver has a full buffer, the window size is reduced to zero. In this state, the window is said to be Frozen and the sender cannot send any more bytes until it receives a datagram from the receiver with a window size greater than 0.
8. If the data is not received as determined by the timer which is set as soon as data is set until receipt of an ACK, then the window size is cut by half. Failure could be due to congestion or faults on the media.
9. On the next successful transmission, the slow ramp up starts again.
Cisco CCENT TCP Reliable Session
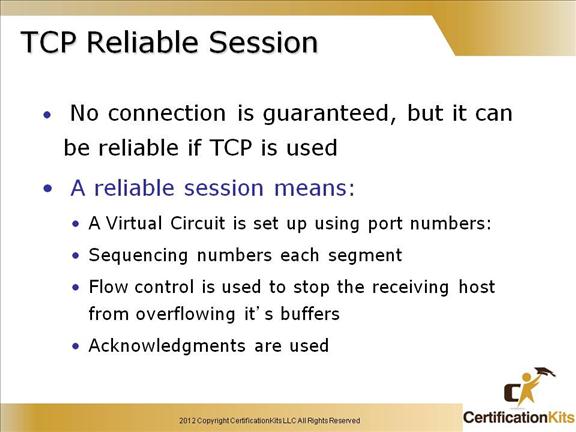
A reliable session is described as follows:
A Virtual Circuit is set up using port numbers
Sequencing numbers each segment
Flow control is used to stop the receiving host from overflowing it’s buffers
Acknowledgments are used
