Cisco CCENT & CCNA Lab Kits – Click Here!
Cisco CCENT TCP/IP Part II – Buffers
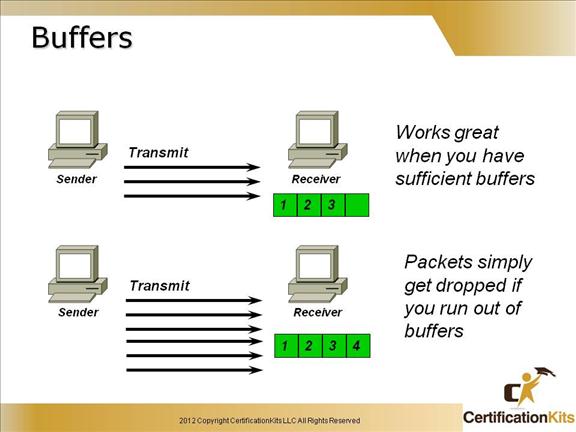
All computers have buffers…the problem occurs when a computer runs out of room in their buffers.
Cisco CCENT Stop and Go
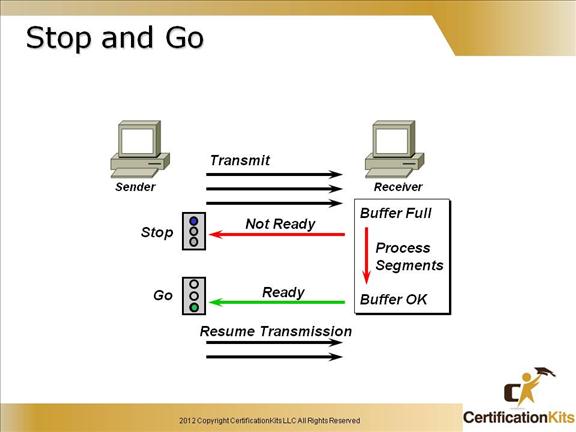
When the receiving host buffers are full, it will send a not ready packet to the transmitting host.
Cisco CCENT Windowing & Acknowledgements
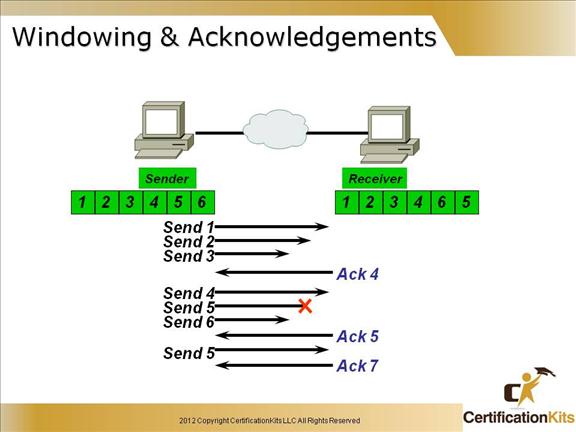
The quantity of data segments (measured in bytes) the transmitting machine is allowed to send without receiving an acknowledgment for them is called a window.
Reliable data delivery ensures the integrity of a stream of data sent from one machine to the other through a fully functional data link.
It guarantees that the data won’t be duplicated or lost.
This is achieved through something called positive acknowledgment with retransmission—a technique that requires a receiving machine to communicate with the transmitting source by sending an acknowledgment message back to the sender when it receives data.
Windowing is used to control the amount of outstanding, unacknowledged data segments.
Cisco CCENT User Datagram Protocol (UDP)
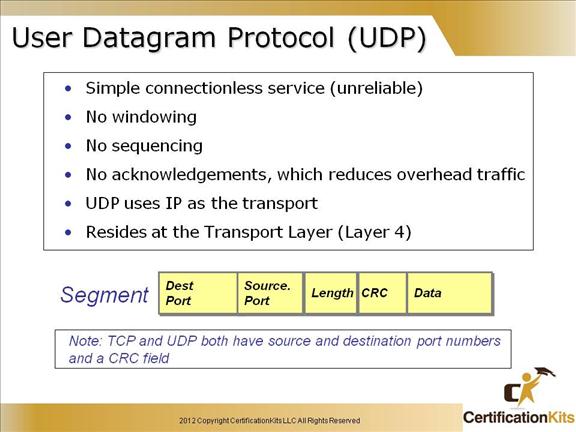
If you were to compare User Datagram Protocol (UDP) with TCP, the former is basically the scaled-down economy model that’s sometimes referred to as a thin protocol.
UDP doesn’t offer all the bells and whistles of TCP, but it does do a fabulous job of transporting information that doesn’t require reliable delivery—and it does so using far fewer network resources.
Like TCP, UDP resides at layer 4 of the OSI model and utilizes IP as the transport. It is a connectionless protocol that does not have windowing, sequencing or acknowledgements which are the things that make TCP a reliable protocol and UDP not a reliable protocol.
Cisco CCENT UDP Header
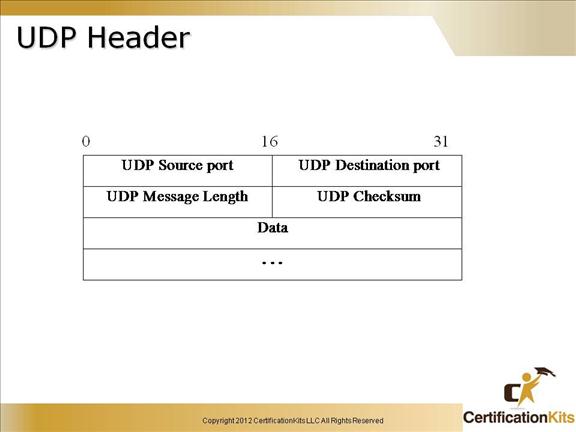
UDP Source port – Optional, when specified, identifies the UDP source port. If not specified, should be zero.
UDP Destination port – Identifies the UDP destination port.
UDP Message Length – The number of octets that comprise user data and the UDP header.
UDP Checksum – Optional, a value of zero means the checksum was not used. Provides a way to ensure the data arrived intact.
Data – User data.
Cisco CCENT Internet Protocol (IP)
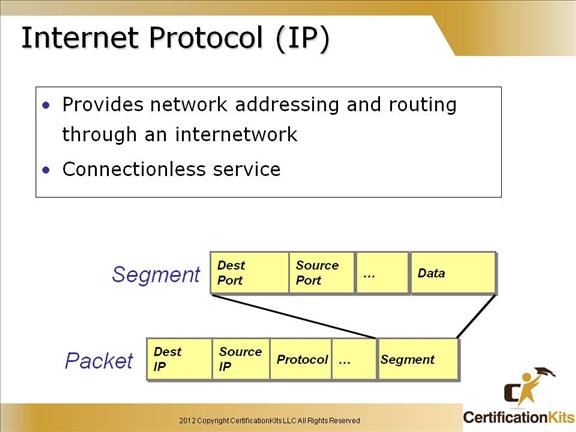
Internet Protocol (IP) essentially is the Internet layer. The other protocols found here merely exist to support it. IP holds the big picture and could be said to “see all,” in that it’s aware of all the interconnected networks. It can do this because all the machines on the network have a software, or logical, address called an IP address, which we’ll cover more thoroughly later in this chapter.
IP looks at each packet’s address. Then, using a routing table, decides where a packet is to be sent next, choosing the best path.
Cisco CCENT IPv4 Header
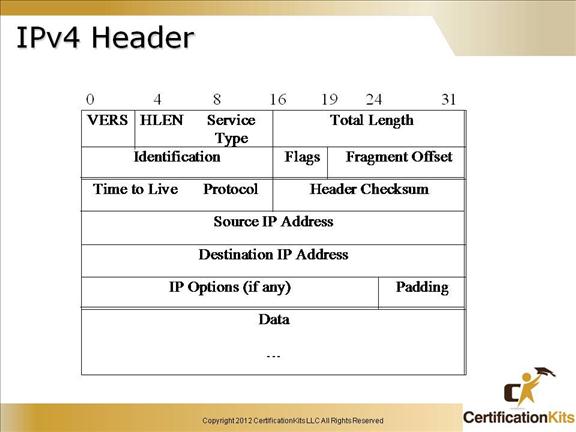
Version – Indicates the version of IP currently used, currently 4
IP header length – Indicates the datagram header length in 32-bit words
Type of service (TOS) – Specifies how a particular upper layer protocol would like the datagram to be handled.
Total length – Length of the entire IP packet in bytes including data and header.
Identification – Used to help piece together data fragments. Contains an integer to identify the current datagram.
Flags – Three bit field used for fragmentation.
Fragment offset -Offset in the original datagram of the data being carried. Measured in 8 octets
Time to live (TTL) – Counter that is decremented as a packet traverses the network. Used to keep packets from looping endlessly.
Protocol – Indicates which upper layer protocol receives incoming packet after IP processing is complete.
Header checksum – Helps ensure IP header integrity.
Source address – IP address of sending node.
Destination address – IP address of receiving node.
Options – Allows support of various options.
Data – Contains upper layer information.
Cisco CCENT Protocol Data Unit (PDU)
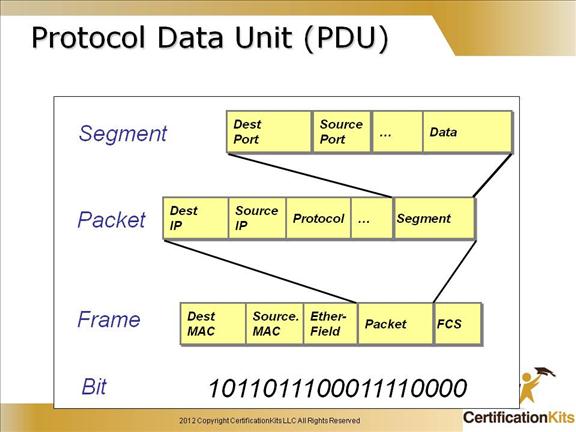
This slide is a review of the protocol data unit (PDUs) at each layer and how data is encapsulated for transmission on the network.
Cisco CCENT Transport and Network Layer
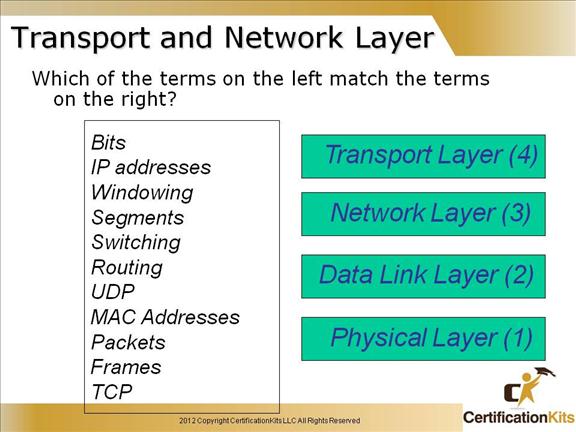
Bits = 1
IP addresses = 3
Windowing = 4
Segments = 4
Switching = 2
Routing = 3
UDP = 4
MAC Addresses = 2
Packets = 3
Frames = 2
TCP = 4
Cisco CCENT Internet Control Message Protocol
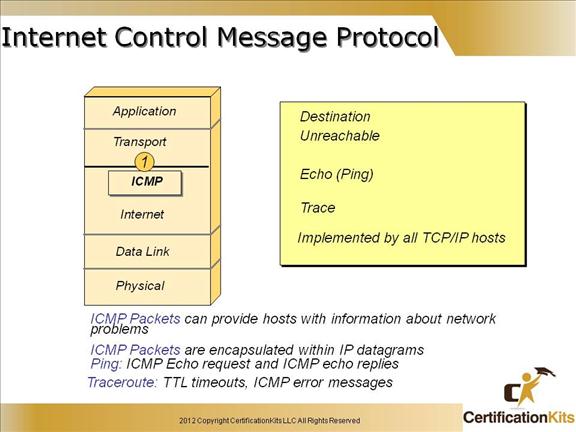
Internet Control Message Protocol (ICMP) works at the Network layer and is used by IP for many different services. ICMP is a management protocol and messaging service provider for IP. Its messages are carried as IP datagrams.
ICMP Packets can provide hosts with information about network problems
ICMP Packets are encapsulated within IP datagrams
Cisco CCENT ICMP Example
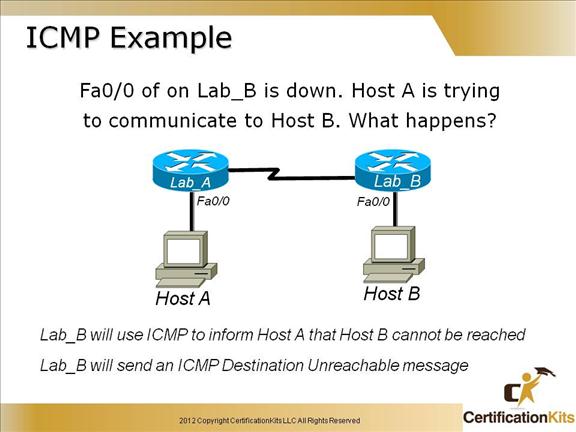
ICMP is used in this example to provide status of packets not being able to be reached to Host B.
Cisco CCENT Network Layer ICMP Message Types
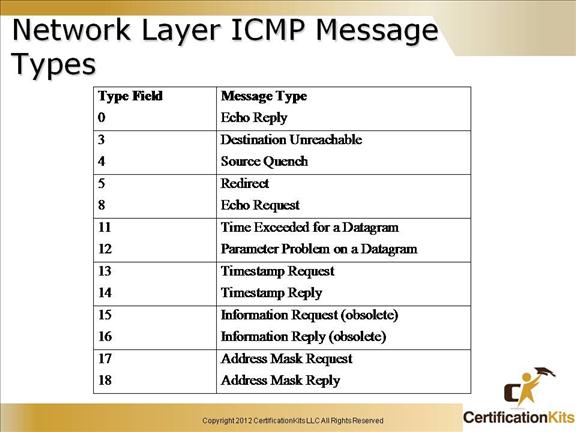
This slide depicts all the ICMP message types. The most common is used by ping which is type 0 (Echo Reply) and type 8 (Echo Request).
Cisco CCENT Address Resolution Protocol
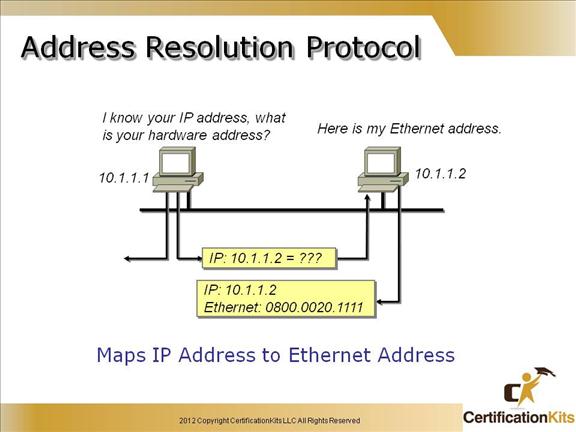
Address Resolution Protocol (ARP) finds the hardware address of a host from a known IP address.
Cisco CCENT Reverse ARP
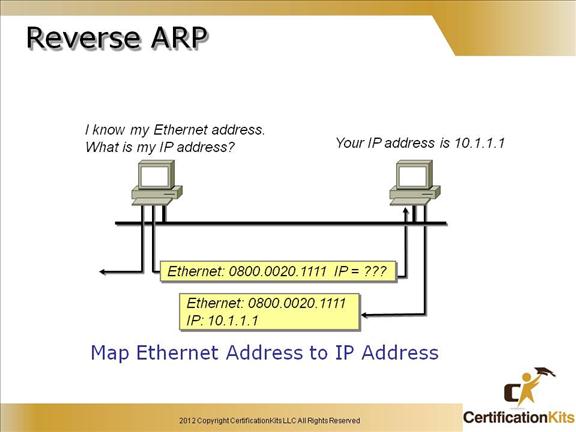
When an IP machine happens to be a diskless machine, it has no way of initially knowing its IP address. But it does know its MAC address. Reverse Address Resolution Protocol (RARP) discovers the identity of the IP address for diskless machines by sending out a packet that includes its MAC address and a request for the IP address assigned to that MAC address.
Cisco CCENT Proxy ARP
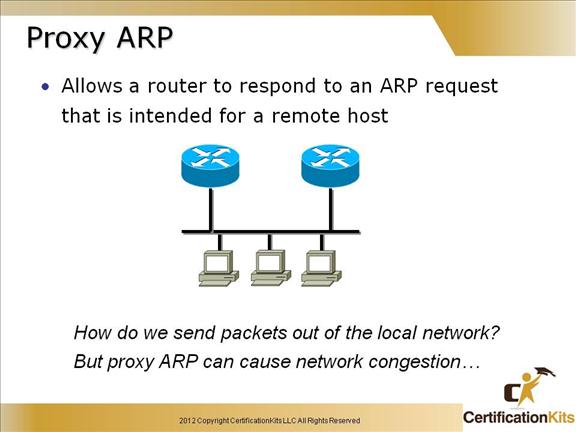
Proxy ARP is the technique in which one host, usually a router, answers ARP requests intended for another machine. By “faking” its identity, the router accepts responsibility for routing packets to the “real” destination.
Proxy ARP can help machines on a subnet reach remote subnets without configuring routing or a default gateway.
Proxy ARP should be used on the network where IP hosts are not configured with default gateway or does not have any routing intelligence.
Cisco CCENT ARP Table on a PC
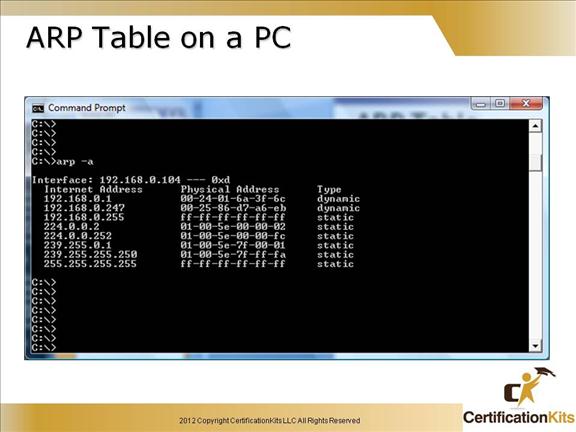
The ARP table will show IP address to MAC address mappings for hosts on the local subnet along with multicast addresses.
Cisco CCENT
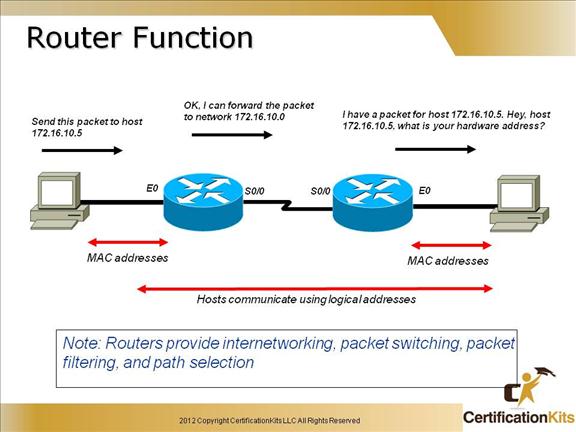
This slides shows how hardware addresses are used by hosts to communicate on a local LAN, and how logical addresses are used to communicate to hosts on remote networks.
Routers use logical addresses to forward packets to remote networks. If a remote network is not listed in a route table of a router, the router will drop any packet destined for that remote network.

