The Deadly Trio
We will take at look at the three main dangerous members of this community namely as follows.
- Worms
- Viruses
- Trojan Horses
Worms & Their Mitigation
Worms are similar in nature to viruses but a bit advanced as far as propagation is concerned. The worm installs itself in the memory of the computer but it has the capability to transfer itself to other hosts automatically even without human intervention, thus making it much more serious than a virus. The only thing to be noted in the case of worms is that they do not spread due to any magic or non-understandable phenomenon, its just that they take advantage of automatic file sending and receiving features that have been enabled on computers in a network either unintentionally or due to some purpose.
Worm Attack Procedure
The anatomy of a worm attack can be broke down into three small steps with far reaching effect and these stages have been listed as follows:
- The first stage goes by the name of enabling vulnerability and is the first step of the process wherein the work gets installed on a vulnerable system.
- After getting installed on a vulnerable system, the worm then spreads its wings further by spreading to new targets. It does so by automatic replication of itself and attacking other systems
- During the last or the payload stage, the hacker tries to raise the level of his/her access. Normally the hackers get to use the targeted system as a privileged user but with the passage of time, they normally aim to have access rights equivalent to that of an administrator and can cause maximum damage after that.
- Once the above cycle is complete, the worm propagates through automatic transmission mechanisms using the vulnerability of the other systems attached to the initially targeted system and the entire process starts all over again.
- Hence in this manner the hacker may be able to gain access to multiple systems and could even use the entire array of such infected systems to cause botnet attacks
The figure below shows a description of such a propagation wherein the network is supposedly safe and secure with a firewall.
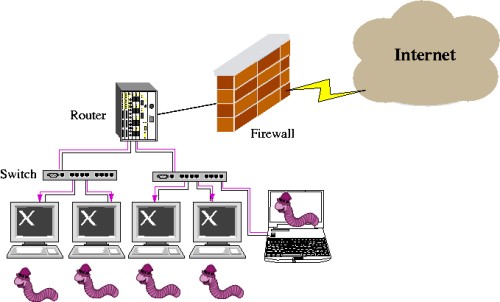
Figure 1: Worm Attack
How to Mitigate Worm Attacks
Due to the specific nature of worm attacks and their methods of self propagation, it is obvious that it would require significantly more intelligent efforts and coordination between the various departments related to network management such as the engineering staff and the security administrators. It would be really difficult if not impossible to control and respond to worm attacks. Proper and systematic planning is necessary for work attack mitigation and normally the process can be divided into the following steps.
Four Steps to Worm Mitigation
- Containment: This step involves compartmentalization of the network into infected and not infected parts. This helps to contain the spread of the worm attack.
- Inoculation: This step involves scanning and patching of the vulnerable systems.
- Quarantine: In this step the infected machine is detected, disconnected and removed. If removal is not possible the infected machines are blocked.
- Treat: This is the step where cleaning up and patching is done. Some worms may need reinstalling of the entire system for a thorough clean up.
The response methodologies for incidents can be categorized into six classes. These classes are based on the response methodology adopted by the network service provider. The classes are enumerated below.
Classes of Response Methodology
- Preparation: This is acquisition of the resources in order to achieve successful mitigation
- Identification: This is identification of the worm.
- Classification: This involves classification of the worm into a specific category.
- Traceback: This refers to a sort of reverse engineering process wherein the source of the worm is traced.
- Reaction: This involves a reaction to the worm in the form of isolation and repairing the targeted systems.
- Post mortem: This involves documenting and analyzing the entire process used. This is done to deal with such attacks in the future.
Viruses
A virus is a piece of deliberately fabricated code which carries out destructive or non-productive task on the computer system to which it gets attached. Similar to biological viruses, computer viruses can get attached to normal programs and modify their behavior in a destructive manner. The only “safe” factor in a virus is that it cannot automatically transmit itself over a network just like worms (as we shall see next) unless there is human intervention. The activities carried out by a virus could be as simple as displaying an annoying or teasing message to the user, or it could be as severe as deleting the entire file system of the computer. This obviously is a serious consequence since valuable data could be lost which could possibly result in a catastrophe if proper backup is not available.
Trojan Horses
The word Trojan horse is taken from the tales of Greek mythology from the Trojan war where solider hid inside the statue of a horse and won over the city of Troy. So as you can gather from the short description of this story, in computer terminology the world Trojan horse is used to refer to those programs which appear attractive and genuine from above, but have malicious code embedded inside them. This code could be either a virus, a worm or both of these.

Figure 2: The Legendary Trojan Horse
The Trojan hose can then be used by the attacker to carry out a variety of nefarious activities from a remote location which could include tampering with the target computer files, stealing passwords, viewing screenshots, getting key-logging reports and so forth.
Some of the ways in which the Trojan horse program could get inside a computer is through embedding in an otherwise genuine program, through email attachments, executable web content such as say the ActiveX controls and so forth.
One of the most notorious Trojan horse programs of the recent times was the Love Bug which originated somewhere from Philippines and infected innumerable computer systems around the globe. Actually this horse contained the worm of a vbs program which caused the damage of nearly 6 billion US dollars and even organizations of the likes of CIA and Pentagon had to shut down their systems temporarily to get rid of it.
Virus and Trojan Horse Attack Mitigation
Virus and Trojan horse attacks can be kept under control by the use of proper precautions such as the usage of proper antivirus software. The following are the few mentioned steps which should ensure that attacks are kept at the minimum threat level, even if not totally eliminated:
- There are a wide variety of antivirus software applications available in the market. Some of them come as stand along software or embedded with a large array of applications known as the Internet Protection Suite. It is important to use some tested and effective antivirus software in order to keep viruses and Trojans at bay.
- Installation of the appropriate software application is necessary but it is certainly not sufficient in order to keep malicious code at bay. Unless these applications are constantly upgraded on a continuous basis and care is taken to keep them in order, they will not be effective against latest threats and attacks. It has been found that with the advancement of technology, the safe period which is available to security personnel between launch of new viruses and threats has been reducing constantly, and currently stands at perhaps a few minutes as compared to a few days or weeks in the past.
- Knowledge is power goes the old but equally wise saying and this is applicable to the network and security administrators as well. They should strive hard to keep themselves updated of the latest threats, attack methods and principles being deployed by hackers. Having such knowledge, they would then be better equipped to deal with such situation and prevent a possible catastrophic situation from emerging.
- Deploying appropriate Intrusion Detection and Prevention systems is also effective in warding off such dangers. One example of this is the CSA or Cisco Security Agent
Intrusion Detection & Prevention
A brief mention has been made in passing about intrusion detection and prevention systems in the previous section about warding of viruses and Trojans. Hence I will be dealing with this area in brief in this tutorial since a detailed study of intrusion prevention and detection has been carried out in a separate tutorial dealing specifically with the broader aspects of the issue from a higher perspective.
It would suffice here to define the basic constituents of these IDS and IPS systems. Basically these stand for Intrusion Detection System and Intrusion Prevention Systems respectively. The main idea behind using these systems is to continuously monitor traffic flow along a network path, normally at the interface between the trusted and the un-trusted sections.
An intrusion detection system is simply a passive system which only monitors activity in the bypass mode, not obstructing traffic directly and only raising an alarm if any anomaly is noted. The IPS on the other hand is an active service which directly intercepts traffic and allows only permitted packets to pass through it, blocking everything else.
These systems can be deployed using appropriate hardware, software or a combination of both. Cisco also offers multifarious devices which play an important role in intrusion prevention and detection.
