Cisco CCNA Why Use ACLs?
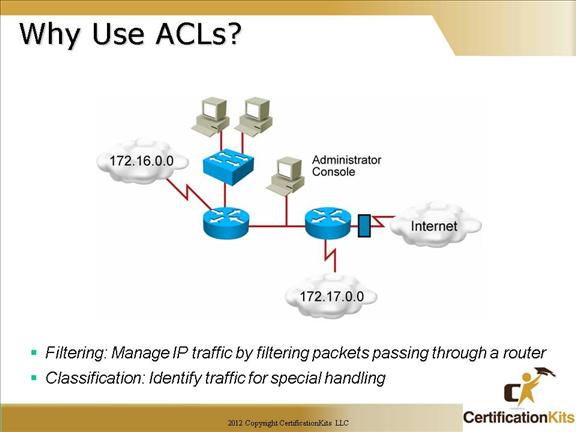
An access list (ACL) is a mechanism for identifying particular traffic. One application of an access list is for filtering traffic into or out of a router interface. There are numerous different types of ACLs. IP standard access lists filter on source ip address only while extended access lists filter on both source and destination ip addresses. You can specify different protocols to filter on (i.e. ip, tcp, udp, icmp, etc.). When specifying tcp and udp, port numbers are chosen to permit or deny specific layer 4 data.
Cisco CCNA ACL Applications : Filtering
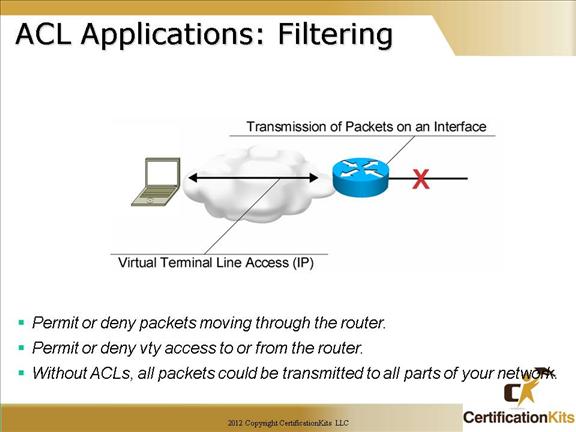
This figure illustrates common uses for IP access lists.
While this chapter focuses on IP access lists, the concept of access lists as mechanisms to control traffic in a network applies to all protocols.
An improved security solution is the lock-and-key access feature, which is available only with IP extended access lists. Lock-and-key access allows you to set up dynamic access lists that grant access per user to a specific source/destination host through a user authentication process. You can allow user access through a firewall dynamically, without compromising security restrictions.
Cisco CCNA Types of IP ACL’s
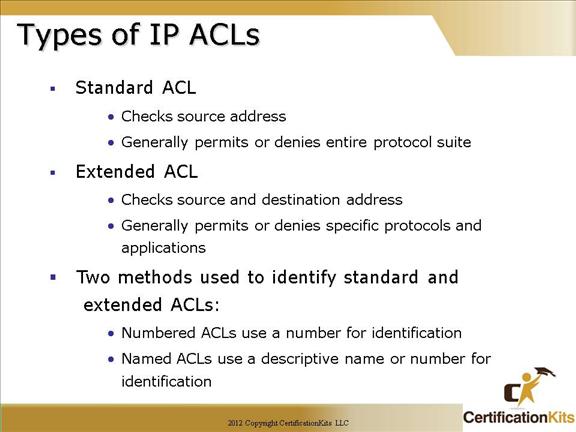
More detailed information regarding standard and extended ACLs are explained on the slides that follow.
Cisco CCNA How to identify ACL’s
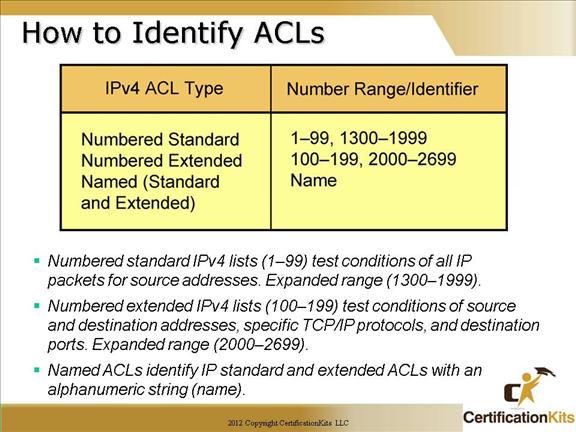
Normal IP access-list range:
IP standard access list range
IP extended access list range
With Cisco IOS 12.0 and later, the IP access-lists range has been expanded to also include:
IP standard access list (expanded range)
IP extended access list (expanded range)
Cisco CCNA IP Access List Entry Sequence Numbering

Cisco CCNA ACL Configuration Guidelines

As a general rule, extended ACLs should be placed close to the source while standard ACLs should be placed close to the destination.
The order of ACLs is very important as each statement is checked from top to bottom and exiting upon the first match. That means the most specific statements should be placed at the top of the list. The last ACL is always an implicit deny so every ACL needs at least one permit statement to be useful.
Cisco CCNA Dynamic ACLs
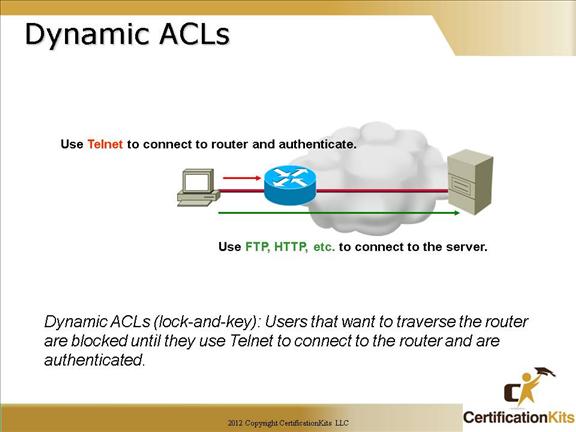
When to Use Lock-and-Key Access
Two examples of when you use lock-and-key access are listed here:
When you want a remote host to be able to access a host in your internetwork through the Internet. Lock-and-key access limits the access beyond your firewall on an individual host or net basis.
When you want a subset of hosts on a network to access a host on a remote network protected by a firewall. With lock-and-key access, you can enable only a desired set of hosts to gain access by having them authenticate through a TACACS+ or RADIUS server.
Lock-and-Key Access Operation
This process describes the lock-and-key access operation.
A user opens a Telnet session to a border router configured for lock-and-key access.
The Cisco IOS software receives the Telnet packet. It performs a user authentication process. The user must pass authentication before access is allowed. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server.
Cisco CCNA Reflexive ACLs
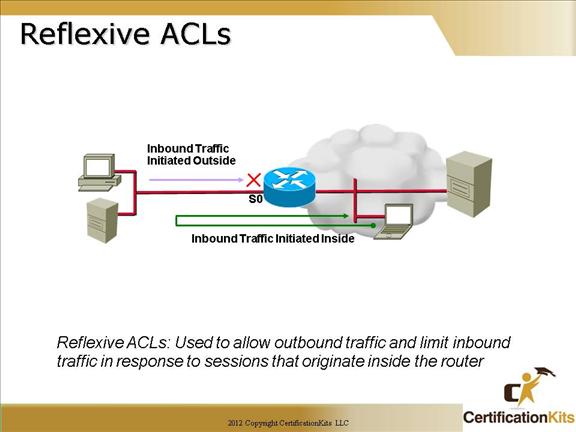
Reflexive access lists are similar in many ways to other access lists. Reflexive access lists contain condition statements (entries) that define criteria for permitting IP packets. These entries are evaluated in order, and when a match occurs, no more entries are evaluated.
However, reflexive access lists have significant differences from other types of access lists. Reflexive access lists contain only temporary entries; these entries are automatically created when a new IP session begins (for example, with an outbound packet), and the entries are removed when the session ends. Reflexive access lists are not themselves applied directly to an interface, but are “nested” within an extended named IP access list that is applied to the interface. Also, reflexive access lists do not have the usual implicit “deny all traffic” statement at the end of the list, because of the nesting.
Cisco CCNA Time-Based ACL’s
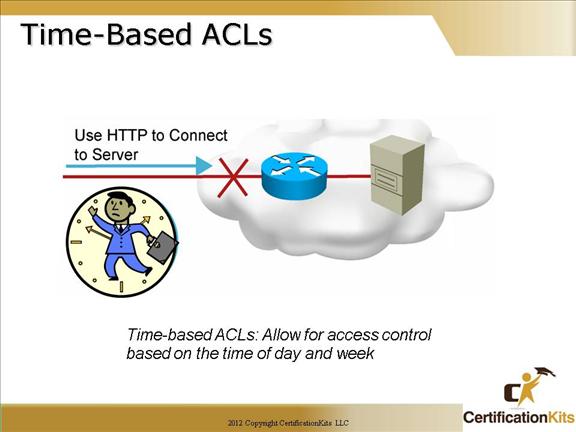
Time-Based ACLs implement access lists based on the time of day. To do so, you create a time range that defines specific times of the day and week. The time range is identified by a name and then referenced by a function, so that those time restrictions are imposed on the function itself.
The time range allows the network administrator to define when the permit or deny statements in the access list are in effect. Prior to this feature, access list statements were always in effect once they were applied. Both named or numbered access lists can reference a time range.
