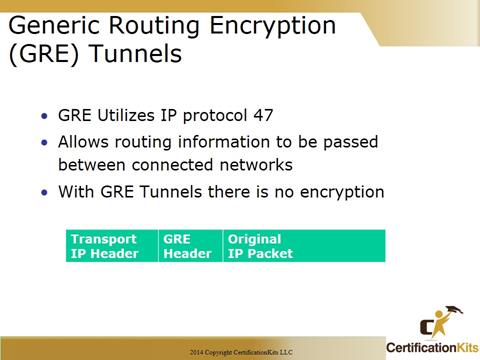
GRE is a Cisco developed protocol which is one of many tunneling protocols. While it is a Cisco developed protocol, it is also defined in several RFCs (1701, 1702 and 2784).
GRE encapsulation supports any OSI Layer 3 protocol. This is a big benefit.
GRE does not include strong security to protect its payload. So you will want to couple this with some other type of technology to protect your data.
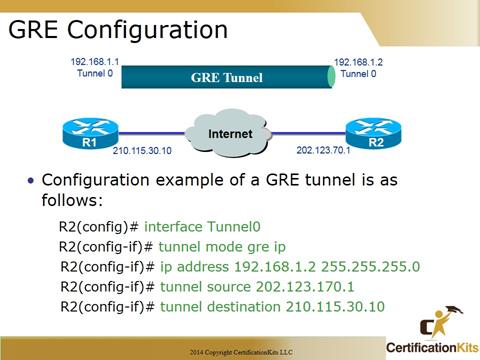
The configuration example in the slide depicts a simple GRE tunnel configuration between routers R1 and R2. Minimal configuration requires specifying the tunnel source and destination (public IP Addresses), a subnet for the tunnel (private IP Addresses) and encapsulation mode (GRE).
R2(config)# interface Tunnel0
R2(config-if)# tunnel mode gre ip
R2(config-if)# ip address 192.168.1.2 255.255.255.0
R2(config-if)# tunnel source 202.123.170.1
R2(config-if)# tunnel destination 210.115.30.10
Some commands the can be used to verify / troubleshoot are as follows:
show ip interface brief | include Tunnel – This command can be used to determine is up or down.
show interface Tunnel 0 – You can also verify the state of this interface with this command. Note: The line protocol on a GRE tunnel interface is up as long as there is a router to the tunnel destination.
show ip route – This command is used to verify there is a router between the tunnel endpoints.