Cisco CCNA Configuring Interface Description
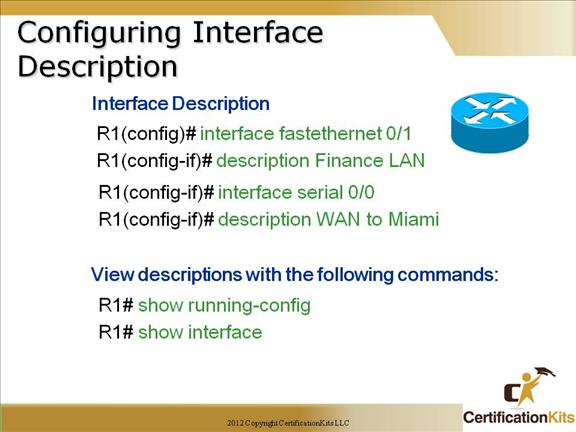
Setting descriptions on an interface is helpful to the administrator and support staff. This is a helpful command because you can use it to keep track of circuit numbers or VLANs for example. If configurations are stored offline, this information can be accessed to create circuit databases, or assist in creation of port maps and network diagrams. Standardizing on the format provides a consistent format in which to create a script to pull the information together into a database, spreadsheet or network drawing.
Cisco CCNA Do the “do”

In IOS versions 12.3 and above you can utilize show commands from within configuration mode by prefixing the appropriate show command with “do”.
Cisco CCNA Console/Aux password Configuration
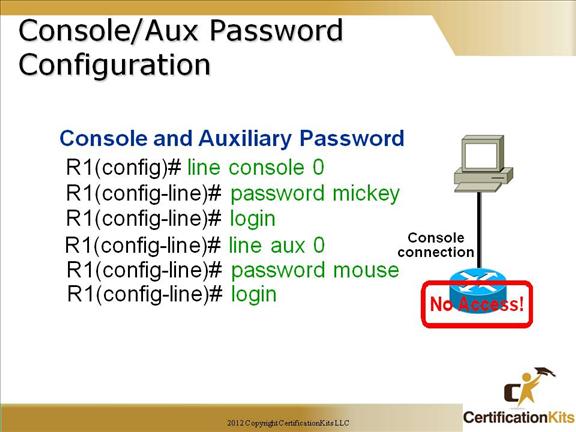
To set the console password, use the “line console 0” command.
Same for the aux port.
You need to enable the “login” command, or the router will not prompt for the password.
Use caution if line passwords are the same as enable secret. Please keep in mind that these will be shown in clear text within the router configuration unless the “service password-encryption” command is utilized from global configuration mode.
Cisco CCNA Other Console Line Commands
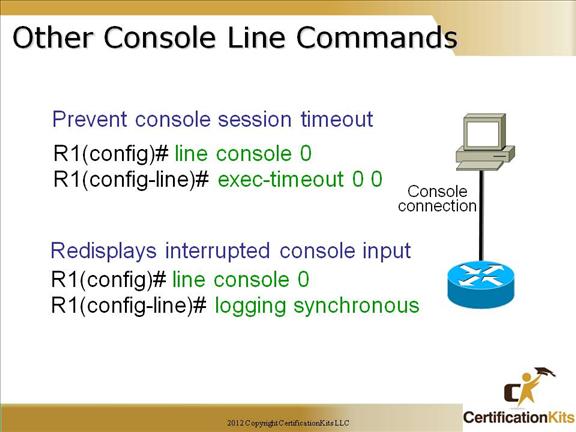
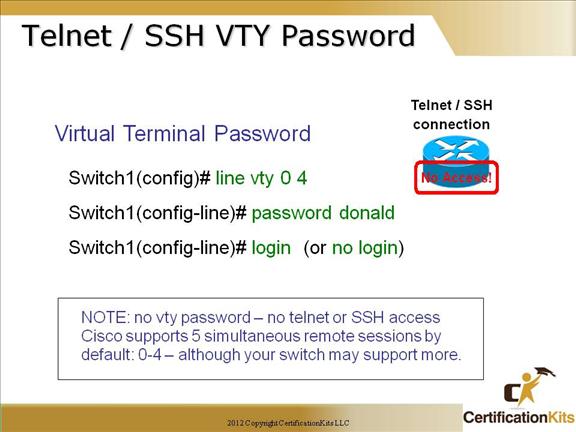
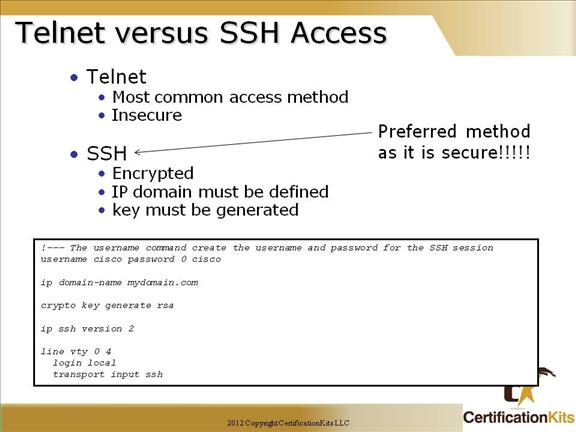
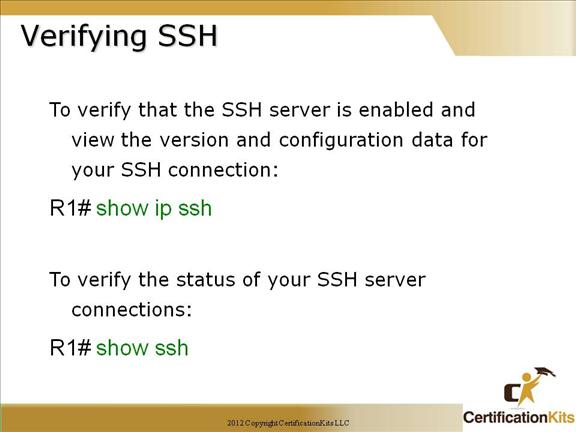
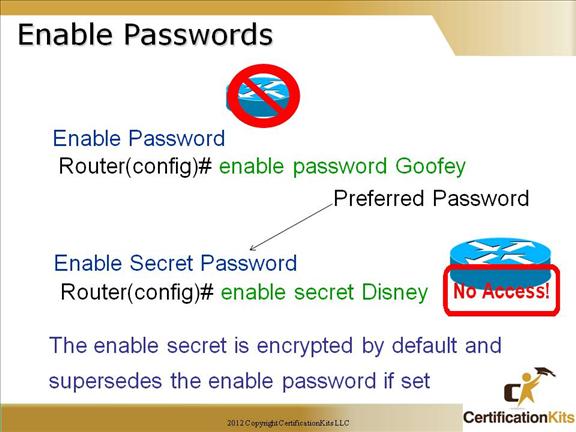
The exec-timeout minutes The logging synchronous command is a very cool command, and it should be a default command, but it’s not. It’s basically stops annoying console messages from popping up and disrupting the input you’re trying to type. After the annoying console message pops up, the current command you were typing is repainted to the screen so you can see the command intact. Said another way, when turned on, unsolicited Cisco IOS software output is displayed on the console or printed after solicited Cisco IOS software output is displayed or printed. Cisco CCNA Telnet/SSH VTY Password To set the user-mode password for Telnet or ssh access into the router, use the “line vty” command. Routers that aren’t running the Enterprise edition of the Cisco IOS default to five VTY lines— 0 through 4. But if you have the Enterprise edition, you’ll have significantly more. The best way to find out how many lines you have is to use that question mark: Router(config-line)#line vty 0 ? Last Line Number You can use the “no login” option so that you can telnet or ssh into a router and not be prompted for a password (not recommended!). Telnet is the most common remote access method but is not secure. All traffic is sent clear text. SSH is a secure remote access method. An access-class can be used on the VTY lines to further restrict access. **Note ** If the password is not set, and TACACS or RADIUS is not configured, you will get “Password not set” when attempting to telnet to the router, and be logged off. Cisco CCNA Telnet versus SSH Access SSH Server The SSH Server feature enables a SSH client to make a secure, encrypted connection to a Cisco router. This connection provides functionality that is similar to that of an inbound Telnet connection. Before SSH, security was limited to Telnet security. SSH allows a strong encryption to be used with the Cisco IOS software authentication. The SSH server in Cisco IOS software will work with publicly and commercially available SSH clients. SSH Integrated Client The SSH Integrated Client feature is an application running over the SSH protocol to provide device authentication and encryption. The SSH client enables a Cisco router to make a secure, encrypted connection to another Cisco router or to any other device running the SSH server. This connection provides functionality that is similar to that of an outbound Telnet connection except that the connection is encrypted. With authentication and encryption, the SSH client allows for a secure communication over an insecure network. The SSH client in the Cisco IOS software works with publicly and commercially available SSH servers. The SSH client supports the ciphers of Data Encryption Standard (DES), Triple DES (3DES), and password authentication. User authentication is performed like that in the Telnet session to the router. The user authentication mechanisms supported for SSH are RADIUS, TACACS+ and the use of locally stored user names and passwords. Cisco CCNA Secure Shell You must remember the command: transport input ssh This enables SSH under the VTY lines. Cisco CCNA Verifying SSH The show ip ssh command is used to verify that the SSH server is enabled and view the version and configuration data for your SSH connection. Example output: SSH Enabled – version 1.5 Authentication timeout: 120 secs; Authentication retries: 3 The show ssh command is used to verify the status of your SSH server connections. Example output: Connection Version Encryption State Username 0 1.5 3DES Session Started guest Cisco CCNA Enable Passwords Setting the Enable password prompts you for a password when you enter the “enable” command from global configuration mode. The “Enable Secret” password is encrypted by default and supersedes the enable password. As a best practice, it is recommended to use the Enable Secret since it is encrypted within the configuration using an MD5 hash. Other means of encrypting the password (level 7) can be easily cracked using shareware programs. This is especially of concern if the configuration files were accessed and the service password-encryption command was not issued which is used to encrypt normal passwords via level 7 so they are not clear text viewable. Use of Enable Secret password is therefore recommended. Cisco CCNA Encrypting your Passwords Remember that you can see all the passwords except the Enable Secret when performing a show running-config on a router if the service password-encryption has not bee issued. To manually encrypt your passwords, use the service password-encryption global configuration command.